thick client security testing tools|thick client lab setup : factory Whether you're a beginner or an experienced security professional, this repository will equip you with the knowledge and tools needed to effectively assess the security of thick client . The latest release for Zimbra Desktop is now available for download. Zimbra Desktop Download. Platform. Download. Windows 64-bit. Zimbra Desktop ( MD5) ( SHA 256) 77.7 MB | Windows EXE Installer. Mac OS X 10.12+. Zimbra Desktop ( MD5) ( SHA 256)
{plog:ftitle_list}
WEB26 de jan. de 2022 · Giassi Supermercados, Jaraguá do Sul, SC . Chamar. Site. Rota. Giassi Supermercados . Rua Expedicionário Gumercindo da Silva, 311, 89252-000 Jaraguá do Sul, SC (47) 3275-5800 . . Rua 13 Maio 400 89255-400 Jaraguá do Sul (47) 3370-5204. Supermercado Duas Meninas 1.33 km Detalhes Site.
Whether you're a beginner or an experienced security professional, this repository will equip you with the knowledge and tools needed to effectively assess the security of thick client . Common examples of thick client applications are video games, audio video editing tools, Microsoft Office, etc. Thick client security .
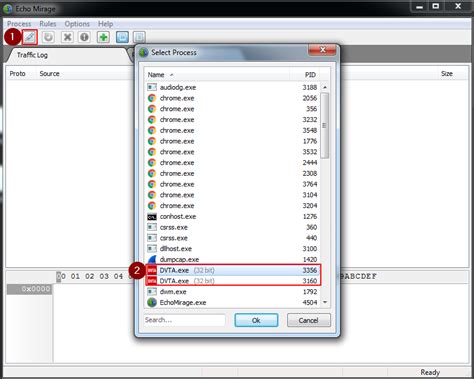
1. Capturing the request via Echo Mirage. Echo Mirage enables intercepting non-HTTP traffic between the tested thick client and the local or remote server. Intercepting requests using this tool, give insight into what kind . In this article, we will learn about thick client applications, their vulnerabilities and ways to carry out security assessment of these applications. A thick client, also known as . Thick client penetration testing is the systematic evaluation of security measures in desktop applications to discover and address vulnerabilities, enhancing the overall security posture of the software and preventing potential .
Tools Used : In our Thick Client Penetration Testing process, we use a diverse set of tools to ensure a thorough and effective assessment. Tools such as Insomnia, Dirb, BurpSuite, Wireshark, Echo Mirage, CFExplorer, Mallory, Nmap, dnSpy, OllyDbg, and Spy++ are integral to our testing process. . Enhanced Integration Security: Thick Client . The thick client app connects directly to the server, bypassing the application server. This architecture is less secure because the end-user has direct access to the data tier. Types of Thick Client Penetration Testing .
API Security Testing: With thick client applications increasingly relying on APIs for communication, there’s a growing focus on API security testing tools. These tools assess the security of the APIs integrated into .
It represents the most common security risks identified in thick client applications. Organizations should adopt this document to ensure that their applications minimize these common risks. Using the OWASP Top 10 is perhaps the most effective first step towards changing the software development culture within your organization into one that .Tools Used. UISpy; Winspy++; Window Detective; Snoop WPF; FILE TESTING. Test For Files Permission. Check permission for each and every file and folder; Test For File Continuity. Check strong naming; Authenticate code signing; Test For File Content Debugging. Look for sensitive information on the file system (symbols, sensitive data, passwords .Some of the common things that we need to do during information gathering phase of thick client penetration test are as follows. Exploring the complete functionality of the application. . Top 10 security tools for bug bounty hunters; Kali Linux: Top 5 tools for password attacks; Kali Linux: Top 5 tools for post exploitation .
When it comes to thick client penetration testing, there are several tools that are commonly used by security professionals. One such tool is Burp Suite, which is a powerful platform for performing security testing of web applications.It provides functionalities like intercepting and modifying network traffic, performing code analysis, and executing exploits.
Sometimes thick client applications use proprietary protocols for communication. Examples of the thick clients are video editing software, video conference software, MS Office, MS Outlook, etc. In this article, we will see the procedure to be followed, vulnerabilities, and tools used for accessing the security of thick client applications.Testing thick client applications for security vulnerabilities requires expert manual penetration testing skills and a thoughtful, methodical approach. NetSPI’s thick client app penetration testing uses multi-vector cybersecurity testing to identify design and configuration weaknesses. What are the security testing methods feasible for Thick Client? We can break down the different types of pen testing a thick client into: Dynamic Testing ( fuzzing, traffic interception, injections) System Testing ( checking for logs, data files, registry keys, process threads) Static Testing ( reverse engineering, binary analysis ) Information gathering is a critical initial phase in thick client application penetration testing, focused on collecting detailed data about the application’s architecture, components, and interactions with servers. . Effective information gathering lays the foundation for a thorough security assessment, enabling testers to identify and .
Read this blog to get insight about thick client penetration testing approach. Covering, enumeration & common tools and vulnerabilities. . Thick Client Pentesting: Architecture, Tools and Testing Approaches. Farid ; June 2, 2021; . CERT-In impaneled Cybersecurity Consulting company specializing in security assessments of IoT product .
Thick client penetration testing is a security assessment process that focuses on identifying and mitigating vulnerabilities in applications that run on client devices, such as desktops or mobile. Madhurendra Kumar. You’ll learn about the thick client, common security risks, great resources for thick client pentesting, popular tools and techniques, andand finally vulnerable labs for practice. Review and Update: Regularly review and update the testing methodology to incorporate new tools, techniques, and best practices. . Thick Client Security Testing: The Essential Guide.
Understanding Thick Client Penetration Testing. Thick client penetration testing is a proactive approach to evaluating and enhancing the security of applications that run locally on a user’s device.
Utilizing the right combination of tools helps penetration testers efficiently assess the security of thick client applications. Best Practices for Thick Client Penetration Testing. To ensure the success and effectiveness of .
Following secure coding practices, using SAST tools to detect security issues at an early stage of development; Removing unused, dead code, test environment details. Following best practice for code comment, clean code approach. Using TPM/HSM or any other secure platforms to store the secrets, keys, etc. I am looking for Application Security Testing (Penetration Testing) of Thick Client Applications. I know of Echo Mirage and ITR as good tools to test these kinda applications. . Best tools for Thick Client Penetration Testing. Ask Question Asked 15 years, 7 months ago. Modified 2 months ago. Viewed 3k times 0 I am looking for Application .Thick Client penetration testing is an ethical hacking security assessment carried out to uncover vulnerabilities in the thick client software application, network traffic, and backend interface and prioritize remediation efforts to mitigate cyber risks.
Selecting the method for Thick Client Pentesting. For thick client penetration testing, there are two key methods: Black-Box Testing: It is the testing approach where the testers initiate the test without any prior knowledge about the app’s configurations.They carry out the testing of all functionalities of the application without any access to design, operation, and . The Thick Client Application Security Testing approach is a highly effective way of testing your client-side software against malware and other threats. The process combines both static and dynamic scanning techniques in order to ensure the safety of the most valuable elements of your application.Due to their reliance on client-side processing, the security of these applications is heavily dependent on the client. Certbar Security offers specialized testing for thick client applications, integrating both DAST (Dynamic Application Security Testing) and SAST (Static Application Security Testing).
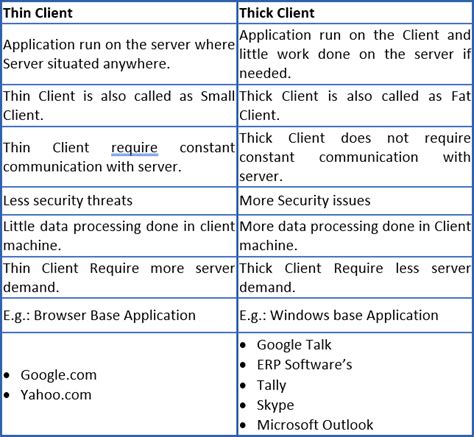
Thick clients are the applications that must be installed on desktops/laptops or servers. These applications can be run on the internet or without the internet. The most common example of a thick client is the installer Skype installed on the desktop/laptop. Other examples of Thick Client are Firefox, Chrome, Microsoft Teams, Zoom, etc. Thin clients. A thick client is a software application that has most of the resources installed locally for processing on typically a personal computer. Thick Clients follows the client-server architecture. . Memory analysis is crucial in penetration testing thick client applications. It involves examining the contents of computer memory when the process . Introduction. The thick client penetration testing tools are used in the penetration testing process of thick client applications that involve both local and server-side processing and are often conducted using proprietary protocols. The attack surface of thick client applications can be extremely large, which can make thick client testing a very exciting .
thick client testing tool
Introduction to Hacking Thick Clients is a series of blog posts that will outline many of the tools and methodologies used when performing thick client security assessments. In conjunction with these posts, NetSPI has released two vulnerable thick clients: BetaFast, a premier Betamax movie rental service, and Beta Bank, a premier finance .
s8 vs pixel 2 drop test
s8 vs s9 drop test
webConfira o melhor prognóstico e palpite para Atalanta x Monza - Palpite Atalanta x Monza se jugarán el sábado 2 setembro para Itália - Serie A.. Abaixo você encontrará a melhor previsão para os mercados vencedores, chance dupla, handicap asiático, os gols marcados por ambas as equipes, os escanteios, os gols de mais/menos de 2,5, as estatísticas de .
thick client security testing tools|thick client lab setup